- Dynatrace Community
- Dynatrace
- Ask
- Open Q&A
- Can you obfuscate a part of a server-side outbound URL?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
Can you obfuscate a part of a server-side outbound URL?
- Mark as New
- Subscribe to RSS Feed
- Permalink
28 Nov 2017
08:54 AM
- last edited on
08 Dec 2021
01:05 PM
by
![]() MaciejNeumann
MaciejNeumann
Hello,
Is it possible to hide a part of a URL? See the blue parts of the below screenshot for an example:
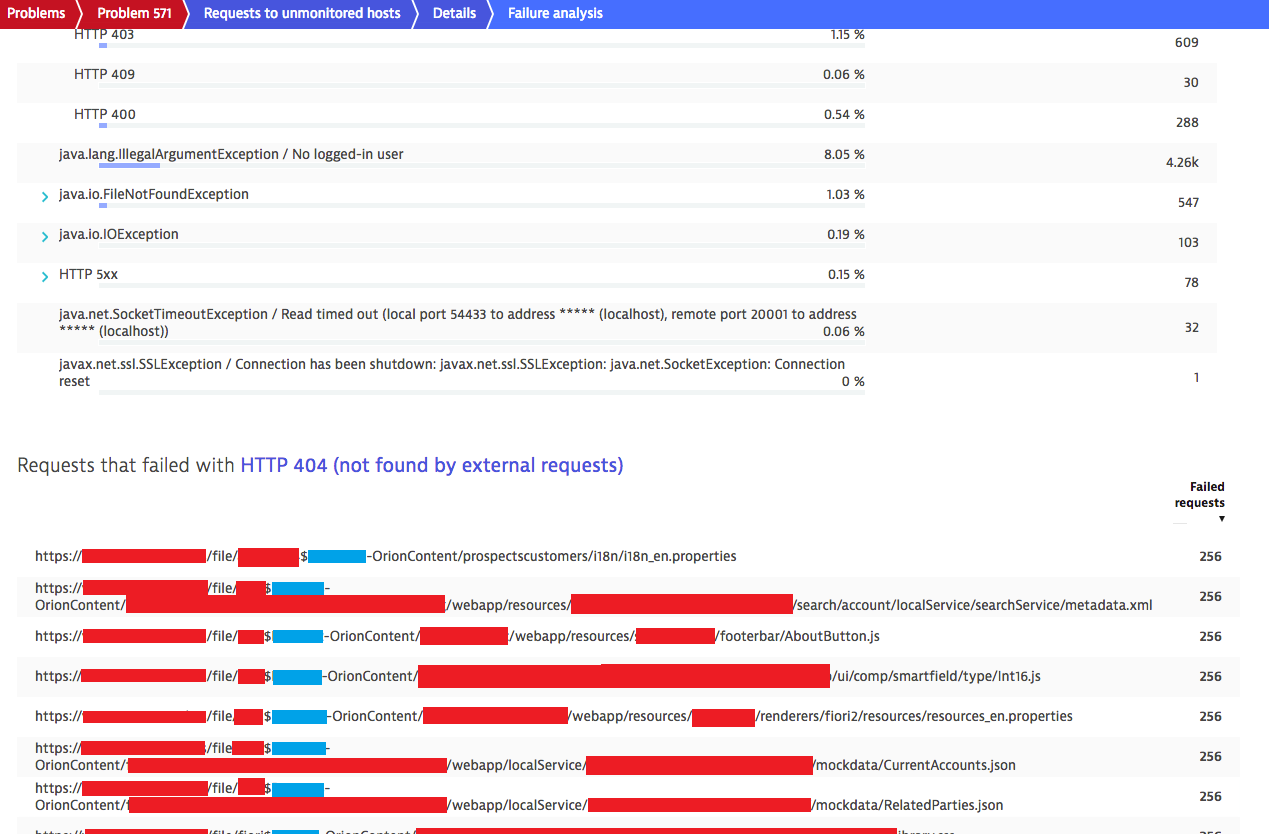
I was considering the Resource URL cleanup rules, but I don't know if that would apply here as it was created for another use case (I cannot test it due to that functionality not being available yet in the cluster).
Kind regards,
Mike
- Mark as New
- Subscribe to RSS Feed
- Permalink
28 Nov 2017 01:31 PM
Hi Mike,
The resource cleanup rules are only available for real user monitoring data.
Alex
- Mark as New
- Subscribe to RSS Feed
- Permalink
30 Nov 2017 05:30 PM
Thanks, I thought as much but I hoped that it could be (mis)-used for this goal 🙂
- Mark as New
- Subscribe to RSS Feed
- Permalink
28 Nov 2017 01:43 PM
is this a cleanup question or security related one?
- Mark as New
- Subscribe to RSS Feed
- Permalink
30 Nov 2017 05:29 PM
Hi Michael, It is a security question.
- Mark as New
- Subscribe to RSS Feed
- Permalink
30 Nov 2017 05:39 PM
GET parameters are obfuscated (replaced by '?') unless you have the "view confidential data" role assigned. POST parameters are never there. Hiding the URLs (or parts of them) would certainly lower value of using Dynatrace as problem solving tool. I can only imagine some cleanup rules (regex), that would mark parts of this URLs as confidential. I don't think this is available in Dynatrace at this time.
- Mark as New
- Subscribe to RSS Feed
- Permalink
30 Nov 2017 05:45 PM
A regex rule that either removes it or at least marks it as confidential would be great. In this case the url's contain usernames of which user owns a bucket (look at it like an S3 bucket). The usernames are never to be linked back to a user action due to regulations.
