- Dynatrace Community
- Dynatrace Managed
- Dynatrace Managed Q&A
- Auditing Dynatrace mission control communication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
15 Dec 2017 08:21 AM
Is there a configuration option or an official utility to audit/dump communication to Dynatrace Mission Control?
Some customers (mostly financial/telco/healthcare) do have strict security policy about communication outside their network and all data uploaded/downloaded to 3rd parties must be audited. Since communication to Dynatrace Mission Control is encrypted, it's not directly possible to see and dump communication payload.
Solved! Go to Solution.
- Labels:
-
dynatrace managed
-
mission control
- Mark as New
- Subscribe to RSS Feed
- Permalink
15 Dec 2017 08:43 AM
I have customer where this will be relevant as well. It was mentioned that it will be possible to intercept the uplink with a proxy and analyze the data.
Is there more concrete information on that?
- Mark as New
- Subscribe to RSS Feed
- Permalink
15 Dec 2017 08:53 AM
Actually the endpoints for outbound communication are specified in the server configuration file. If you use a classic MITM proxy, it will probably not work because of certificate validation. You would have to add a custom certificate to truststore for Dynatrace server and maybe other components as well.
If Dynatrace server allows changing those endpoint urls (billing, opc, ...) to non https, it would be quite simple to write a "proxy" to dump communication and forward it to mission control. However not sure about the websocket communication from Dynatrace into customer environment.
Probably both methods can be used, but I'm asking for official supported solution.
- Mark as New
- Subscribe to RSS Feed
- Permalink
15 Dec 2017 09:09 AM
There is no generally available tools to dump the clear text payload sent to Mission Control. We can discuss internally what's inside each request.
Please also read new topic in documentation "How does Mission Control pro-active support work?" and
https://www.dynatrace.com/support/help/get-started...
in particular:
Dynatrace Mission Control is responsible for sending
- Usage and billing information.
- Dynatrace Server health statistics
Once permission is granted, our Mission Control team can remotely
analyze the hardware utilization of your Dynatrace Managed installation
and alert you if more resources are required. - Dynatrace Server event tracking
Events like server starts/shutdowns, added/removed nodes, and Security
Gateway registrations are tracked automatically. Our Mission Control
team can remotely analyze and address problems or incompatibilities with
your Dynatrace Server, so you don't need to track and react to system
events. If you should ever need to contact Dynatrace Support, you won't
need to collect the required log files for problem details—Mission
Control gathers this data for your automatically. To see the list of
Dynatrace Server system events that are automatically logged, click the Events tile on your Dynatrace Managed home page. - System settings
Our Mission Control team can remotely optimize your Dynatrace Managed settings to ensure optimum performance and stability. - Software updates
Dynatrace Managed software updates are mandatory and are typically
published every four weeks. You can customize the timing of Dynatrace
Managed updates (daily or weekly). Updates are automatically
communicated to your users at least 24 hours in advance. Dynatrace
Managed updates are fast and allow monitoring to continue seamlessly.
Dynatrace Managed expert
- Mark as New
- Subscribe to RSS Feed
- Permalink
15 Dec 2017 09:33 AM
@Radoslaw S. could you ping me so we can discuss the possibilities of intercepting the mission control traffic? patrick.hofmann@amasol.de
- Mark as New
- Subscribe to RSS Feed
- Permalink
15 Dec 2017 09:38 AM
I'm aware what is mission control used for.
However this answer won't be acceptable by security personnel in environments with high security requirements (agents on servers processing sensitive data, such as banking).
Not being able to audit communication will likely prohibit Dynatrace for being deployed (=purchased) in such environments.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04 Jun 2018 03:11 PM
Do we have any update on this? Would like to get more details how the data can be audited and what type of flexibility is available in what information can be sent from the managed server.
- Mark as New
- Subscribe to RSS Feed
- Permalink
04 Jun 2018 03:32 PM
There is flexibility, observe the preferences available to a cluster admin in the CMC. There is also complete audits available to cluster admins in the CMC (observe audit log in the sidebar in pic below).
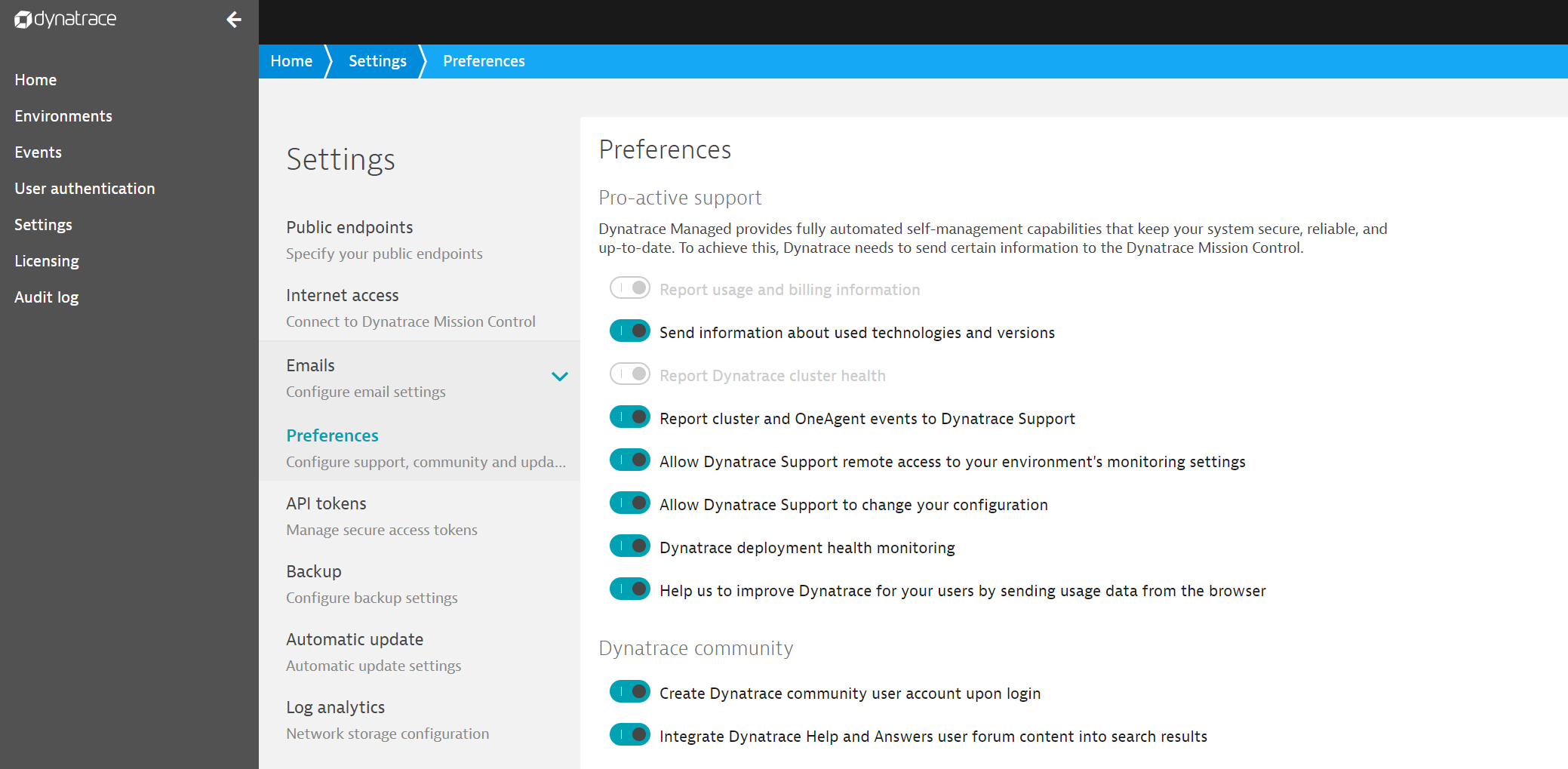
As above mentioned by Radoslaw, check the Mission Control Security section.
Dynatrace have provided further insight in the Trust Center, if you are interested in this subject.
- Mark as New
- Subscribe to RSS Feed
- Permalink
17 Sep 2019 04:38 AM
- Mark as New
- Subscribe to RSS Feed
- Permalink
17 Sep 2019 07:40 AM
Nothing has changed, but you can still do MITM communication auditing. It requires some work with adding a certificate to the trust store so Dynatrace Cluster can trust the MITM proxy.
Anyway, any changes from Dynatrace are being audited in the Audit log available in the CMC.
- Mark as New
- Subscribe to RSS Feed
- Permalink
17 Sep 2019 05:55 AM
Some of our clients are unsecuring communication to mission control and tracking it for some time. After that they are going back to normal. I don’t know any other option.
Sebastian
