- Dynatrace Community
- Dynatrace
- Ask
- Open Q&A
- Dynatrace Proposed Design Assistance Required
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
Dynatrace Proposed Design Assistance Required
- Mark as New
- Subscribe to RSS Feed
- Permalink
09 Jul 2018
01:56 PM
- last edited on
09 Dec 2021
01:06 PM
by
![]() MaciejNeumann
MaciejNeumann
Dear All,
We need your expert advises to design a robust setup for the Dynatrace e.g. we have multiple network zones of PCI/Non-PCI for the web servers /application servers /database servers and few of them are heavily used and some of them are comparatively less.
Our idea is to deploy 2 x ActiveGate (to get the advantage of load balancer / failover) in the heavily used zones and 1 x ActiveGate in others.
So in the same zone we do not need to open the port # 9999 from OneAgent to the ActiveGates and we can open only a port # 8443 from OneAgent to the Dynatrace Cluster.
In case one of the ActiveGate goes down in the heavily used zones then the agents should connect to the next available ActiveGate and if both are not available then it should connect directly to the Dynatrace Servers Cluster and the same should apply on the less utilized zones.
Please have a glance on the below diagram and also let us know that how the ActiveGate is talking to the Dynatrace Servers Cluster and on which TCP/IP port.
Note: A correction in the diagram that Zone A will have 2 x ActiveGate and Zone B will have 2 x ActiveGate.
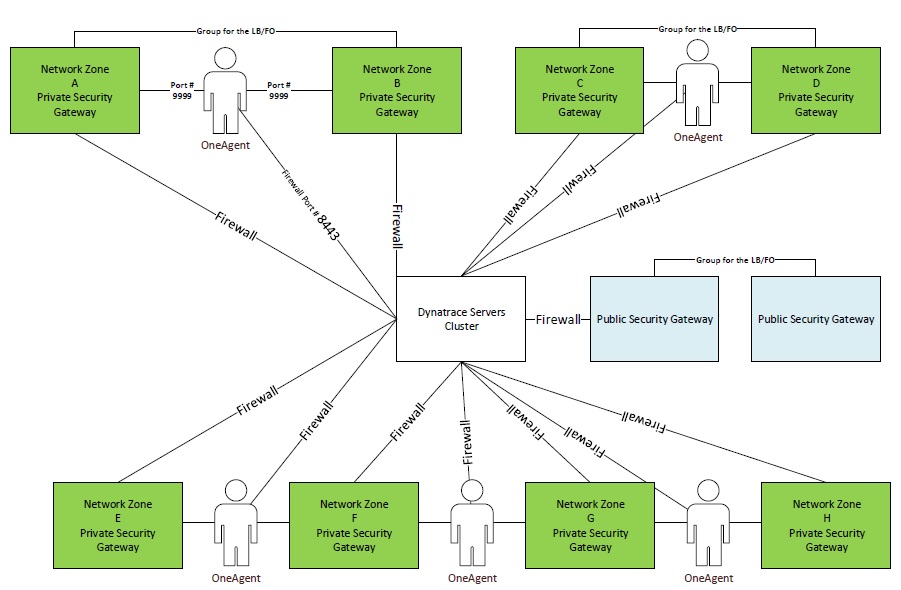
Regards,
Babar
- Labels:
-
activegate
-
oneagent
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jul 2018 09:08 AM
The Private Security Gateways will talk to the Dynatrace Managed Cluster on Port 8443.
So if they are in the same network as the agents, and the agents can talk to the cluster anyway you are all set.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jul 2018 09:22 AM
Hello @Patrick H.
Please correct my understanding about the following:
- Private Security Gateways and OneAgent talk to the Dynatrace Managed Cluster on Port 8443
- If Private Security Gateway is available in the same network zone then initially OneAgent will try to connect to the SGW and in case of absence will connect to the Dynatrace Managed Cluster
Regards,
Babar
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jul 2018 09:29 AM
Correct, though I'm not 100% sure it will always prioritize the SGW. I'm sure someone can clear this up though.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jul 2018 10:33 AM
Hello @Patrick H.
Thank you for your comments. Maybe someone else can share with us a real time experience.
Regards,
Babar
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jul 2018 12:25 PM
Real time experience - Yes - for agents, connecting to private gateway has the highest priority. If no private gateway is reachable, the agent tries to connect to any of public gateways (if you have them in the environment). Connecting directly to cluster has the lowest priority.
Actually, if you look carefully at the endpoint list (serverAddress in ruxitagentproc.conf) it is sorted with the priorities above. Private > Public -> Cluster.
Agents do not check network hops (my experience) nor calculate subnets. Maybe they check network RTT to prioritize some private gateways before others.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jul 2018 12:58 PM
Hello @Julius L.
Currently, we are planning to setup the Dynatrace environment, therefore, maybe can ask some silly questions.
Below statement is about the dnsEntryPoint of the security gateway. We do have Public Security Gateways in our designed environment, so how the agent will connect to the Public Security Gateway in case Private Security Gateway is not available and according to the sequence Private > Public -> Cluster.
Define the entry point for the Security Gateway (for example, http://sg1.mydomain.com:9876). Via this URL, the Security Gateway is accessed by Dynatrace OneAgent. If not set, an auto-detected endpoint will be used. This entry can be used if the Security Gateway is accessed via, for example, an external IP address or load balancer.
Regards,
Babar
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jul 2018 01:24 PM
AFAIK, if the dnsEntryPoint is specified during installation or afterwards in the gateway config, only this entry gets propagated to the endpoint list. So the agent will only try to connect to the address and port (and IPs) specified by the dnsEntryPoint.
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jul 2018 01:40 PM
Hello @Julius L.
So by defulat the same entry point will be used for the Public Security Gateway as per the sequence Private > Public -> Cluster?
Regards,
Babar
- Mark as New
- Subscribe to RSS Feed
- Permalink
10 Jul 2018 01:46 PM
I can't try it now in my lab, but I this dnsEntryPoint works that way with private SGW. I expect this behaves equally for public SGW.
