- Dynatrace Community
- Dynatrace
- Ask
- Cloud platforms
- setting up Azure sso SAML integration with Dynatrace
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
30 Jun 2023
11:09 AM
- last edited on
03 Jul 2023
07:38 AM
by
![]() MaciejNeumann
MaciejNeumann
I am currently in the process of setting up Azure SAML integration with Dynatrace, following the steps outlined in your documentation.
However, I am encountering an issue and would appreciate someone's assistance in identifying any missed configurations or potential errors on my part.
Azure SAML Configuration:
- Created the SAML group in Azure matching the security group claims.
- Configured the necessary SAML attributes and claims in Azure.
Dynatrace Configuration:
- Configured the Azure AD application in Dynatrace, providing the appropriate SAML settings.
- Configured the required attribute mappings and mappings for group claims.
Error Message:
- Upon attempting to authenticate with Azure SAML, I receive the following error:
needs permission to access resources in your organisation that only an admin can grant. Please ask an admin to grant permission to this app before you can use it.
My understanding to the error is I can login to Dynatrace via Azure AD (authentication passed), but my login has no admin permission (authorization) is INCORRECT, please correct me if I am wrong
Solved! Go to Solution.
- Labels:
-
account management
-
azure
-
sso
- Mark as New
- Subscribe to RSS Feed
- Permalink
07 Jul 2023 02:32 PM - edited 07 Jul 2023 03:00 PM
Need admin approval
needs permission to access resources in your organisation that only an admin can grant. Please ask an admin to grant permission to this app before you can use it.
means that you used OpenId authentication via Sign in with MIcrosoft (which redirects the federated user to SAML, but only after successful OpenId authn on Azure side), instead of the direct SAML authentication initiated by providing email in the Dynatrace login form. Please use the second and let us know if it helps.
Regarding the message: it is caused by the Azure Tenant configuration. More info:
https://learn.microsoft.com/en-us/azure/active-directory/develop/application-consent-experience
https://learn.microsoft.com/en-us/azure/active-directory/develop/permissions-consent-overview
https://learn.microsoft.com/en-us/azure/active-directory/manage-apps/user-admin-consent-overview
- Mark as New
- Subscribe to RSS Feed
- Permalink
28 Jul 2023 10:14 PM
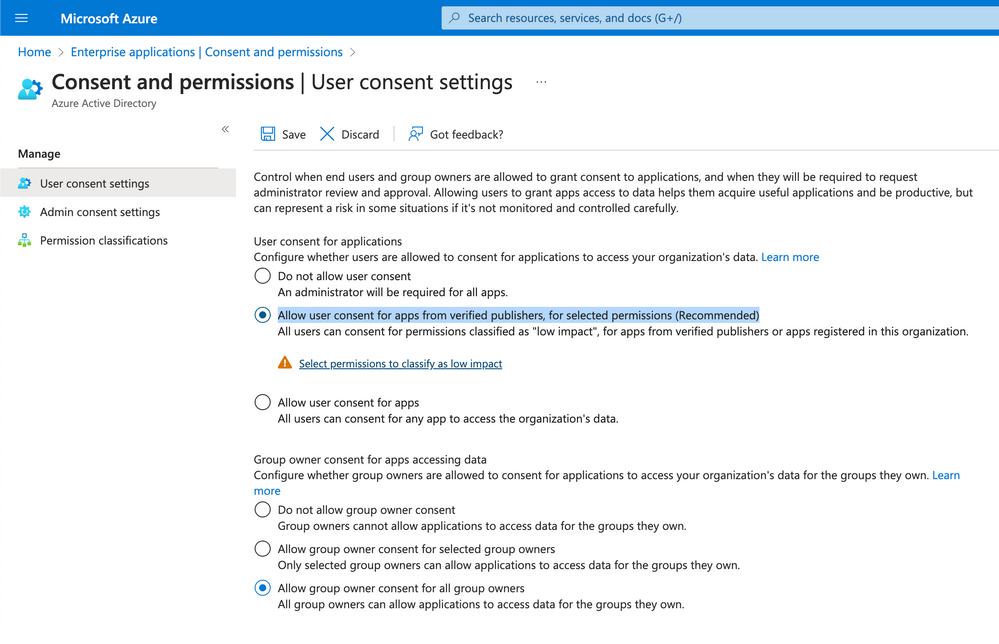
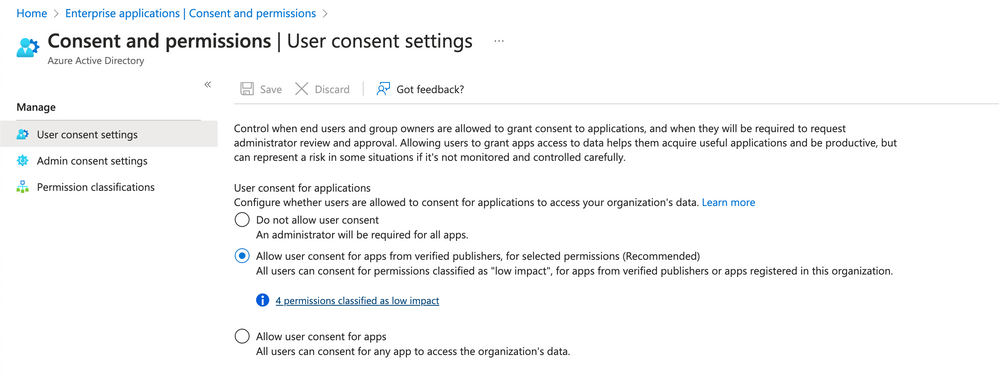
I recently tried to reproduce the issue to provide a guideline how to configure Azure AD to allow the user to consent on their to using the Dynatrace application and thus being able to log in through "Sign in with Microsoft". It seems that the Azure administrator has to change the "Enterprise applications" -> "Consent and permissions" to "Allow user consent for apps from verified publishers". We have made sure that our application is verified, so this option applies.
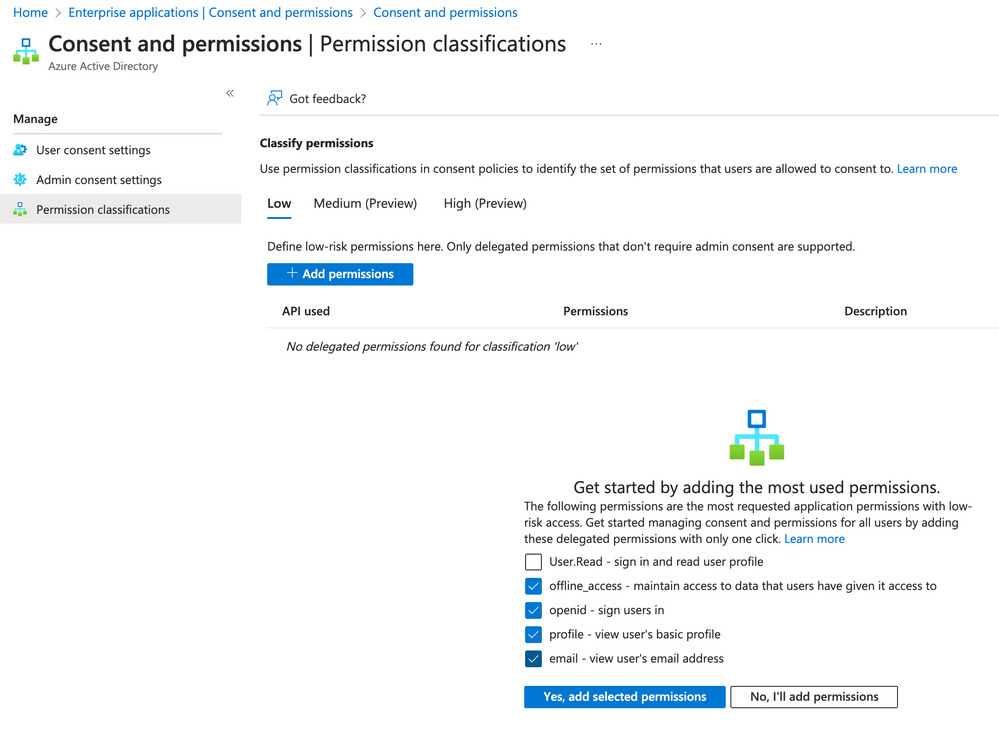
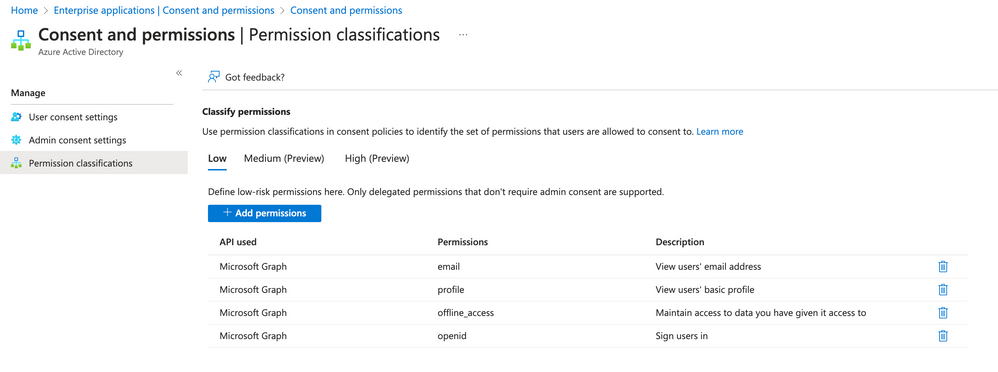
Then, we require the following "low impact" API permissions to be allowed to be constented to by users:
- offline_access
- openid
- profile
They are required, because Dynatrace SSO has to be able to access basic information about the user, who is logged in to Azure to create a session in Dynatrace as well.
Once the permissions are configured, this is how the "Consent and permissions" screen would look like.
This should allow all users from your Azure tenant to log in and instead of "Need admin approval", there should be a message that shows the "Permissions requested" and an "Accept" button, which would finalize the login in Dynatrace SSO.
Note that this consent screen is shown only once for each user, who decides to access Dynatrace through the "Sign in with Microsoft" option.
As far as I was able to figure out in Azure, the consent and API permission options cannot be set per application (e.g. only for Dynatrace), but apply either to all verified applications or the constent has to be approved by the admin. I would suggest to contact Azure's support directly, if the organization cannot agree to set it up as proposed above, to get the any possible alternative solutions.