- Dynatrace Community
- Dynatrace
- Ask
- Container platforms
- Separate multi-tenant log data with management zones
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
Separate multi-tenant log data with management zones
- Mark as New
- Subscribe to RSS Feed
- Permalink
17 Jul 2023
09:17 AM
- last edited on
19 Apr 2024
12:12 PM
by
![]() Michal_Gebacki
Michal_Gebacki
- Labels:
-
kubernetes
-
logs
-
management zones
- Mark as New
- Subscribe to RSS Feed
- Permalink
18 Jul 2023 04:57 PM
Hi, its more about data ownership. That the people in one management zone can only read their own data (logdata) regardless of the form of the data. In our case this is json and syslog compatible logging, but that is only important for processing.
- Mark as New
- Subscribe to RSS Feed
- Permalink
02 Aug 2023 10:18 AM
We've made a feature request and we are investigating some new possibilities:
https://community.dynatrace.com/t5/Product-ideas/opt-in-logging-using-kubernetes-labels/idi-p/219533
- Mark as New
- Subscribe to RSS Feed
- Permalink
08 Aug 2023 10:26 PM
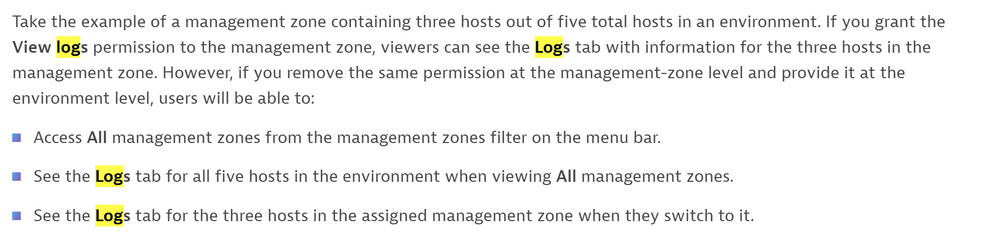
Hello PeterR,
Is this something you are looking for?
The source:
https://www.dynatrace.com/support/help/manage/access-control/manage-user-permissions-roles
- Mark as New
- Subscribe to RSS Feed
- Permalink
09 Aug 2023 09:17 AM - edited 09 Aug 2023 09:18 AM
Hi, unfortunately no. In Kubernetes, tenants are separated by data ownership on a application level like namespaces, labels and annotations. Not underlying hosts. Pods and containers share underlying hosts. It's an abstraction layer so to speak. But thanks for your reply.