- Dynatrace Community
- Dynatrace Managed
- Dynatrace Managed Q&A
- Dynatrace Managed - certificate update
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Pin this Topic for Current User
- Printer Friendly Page
- Mark as New
- Subscribe to RSS Feed
- Permalink
19 Feb 2021 12:47 PM
Hi,
For a Dynatrace Managed installation we have to import custom certificates (which are signed by the company itself). By doing this, the connection to Mission Control was succesful.
Afterwards we remarked that the remoteaccess and the OneAgent (on the cluster node) were not updated automatically and didn't work as expected. In the log file we saw that the certificate check failed in both cases.
In the end, we had to update the certificates of all 3 components (dynatrace-managed jre, remoteaccess jre and oneagent) seperately in order to update them.
Wouldn't it be more logic and efficient to provide a script to update all of them? Or, even better, that the 3 components use the same trusted store?
Kind regards,
Jurgen
Solved! Go to Solution.
- Labels:
-
dynatrace managed
- Mark as New
- Subscribe to RSS Feed
- Permalink
19 Feb 2021 01:40 PM - edited 07 Nov 2023 10:49 AM
Hi @Jurgen R. !
Thanks for the question! To be on the same page, we need to distinguish and clarify 2 aspects of communication from/to the Dynatrace Managed cluster:
1) Outgoing - from the cluster to Mission Control. In your case that's a communication through a proxy/LB server. If the proxy server runs on secure connection (HTTPS) and the connection is verified by a custom self-signed certificate, then all Dynatrace Managed cluster nodes has to import the proxy certificate in order to trust it (otherwise someone else could spy the traffic).

2) Incoming - from OneAgent / ActiveGate / UI / REST API to cluster. The use case here is that you want to secure all connection incoming to the cluster - so all clients (AGs, OA, users) can trust they connect to the cluster. Cluster nodes run also on HTTPS communication and use SSL certificate provided by you or automatically provided by Dynatrace.
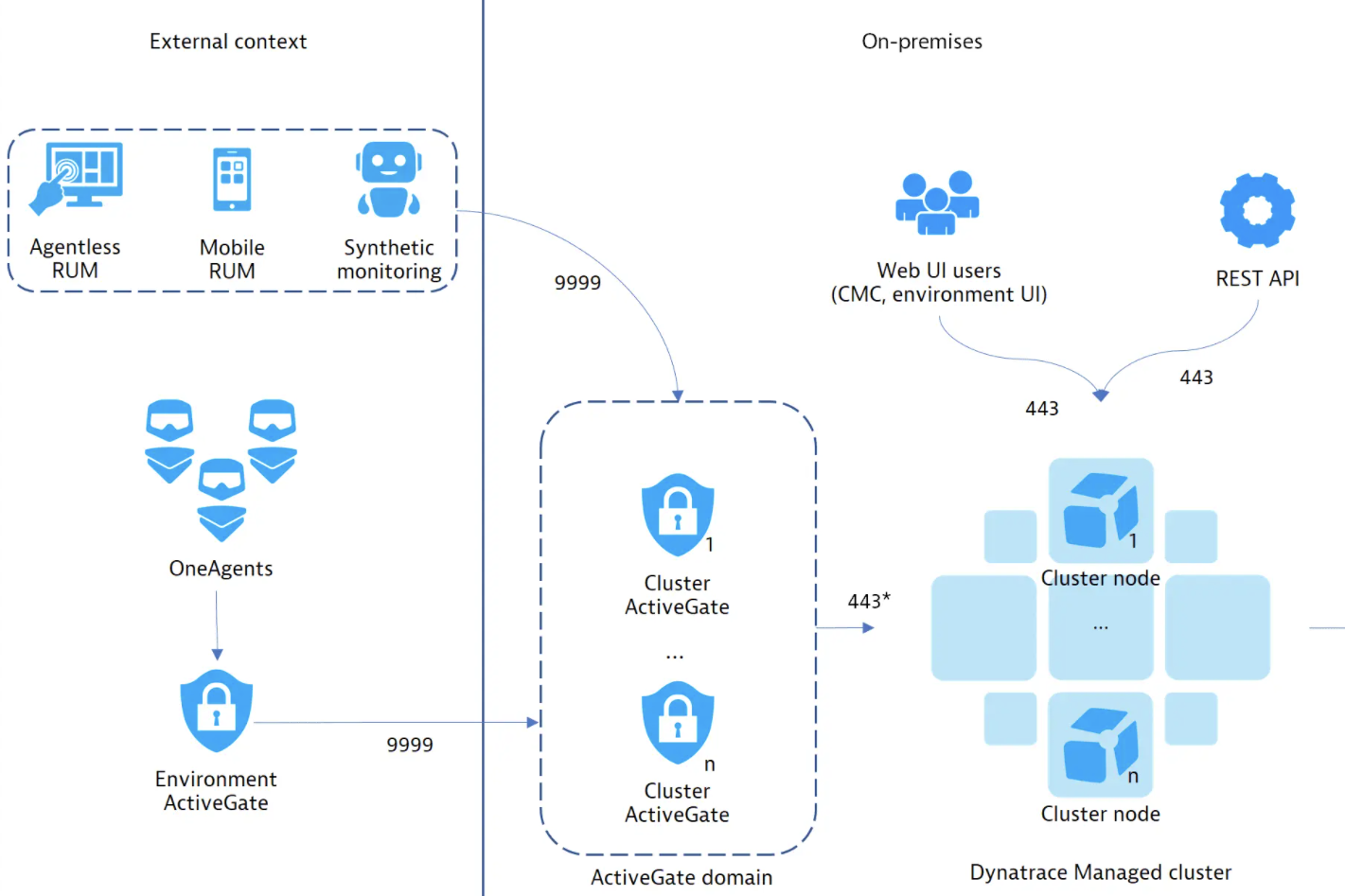
Now:
- In order to install Dynatrace Managed, you have to ensure the cluster can communicate securely to Mission Control. Installer uses OS native communication to connect to Mission Control. By providing the cert to proxy, we store in the system so it can be reused e.g. during next upgrade. It's also automatically imported to cluster nodes Java keystores (again - other technology).
- In order to apply a custom certificate for incoming communication you use CMC UI or REST API to provide SSL certs to all nodes. You provide a "cluster SSL Certificate" once, and certificates are distributed to all nodes automatically. Details:
https://docs.dynatrace.com/managed/managed-cluster/configuration/how-to-add-a-certificate-to-server-...
To sum up, proxy cert and cluster certs are different SSL certificates, handled differently for a different purpose. We've provided you means to do it once per a certificate (proxy or cluster), and Dynatrace takes care of update all places that are applicable. We don't expect our users know all internal places that need to be updated with a SSL cert. If there's a place that was not updated - it's a defect in the product and contact support/Dynatrace ONE that something doesn't work as expected.
PS For the time we discuss I've moved your post to the Q&A Forum as a question. Currently I'm not still sure if that's a valid request for an enhancement.
Dynatrace Managed expert
